The Battle Against Viruses Takes to the Cloud
After a brief summer break, I start again this week with a weekly post; or so I plan.
This week, the topic revolves around antiviruses and the battle that all AV companies are inequivocably losing.
Traditional Antivirus Solutions
Traditional antivirus technologies focus on recognizing the threat, identifying it properly, and then stopping it. They rely heavily on human beings analyzing pieces of malicious code and creating “signatures.” The entire process of finding malicious code, analyzing it, creating the signature, testing it properly and deploying it can take between 4 and 12 hours. Hackers know this and are taking advantage of it by flooding the Internet with new code at a rate that we now calculate to be about 40,000 new pieces of malware per day. This is unprecedented and is causing the traditional antivirus companies to lose their battle against malware writers, by a very large margin.
To give you an idea of how dismal the situation is, we calculate that every day there are at least 80,000 pieces of malware that no one has signatures for. Which means, if one of these makes its way to your computer, not only will your AV not stop it, but it may not even recognize that a malicious piece of code was installed on your computer. Days later, when you perform a system-wide scan, if your AV has a signature, it may recognize that malicious code. Clean up is often out of the question; quarantining is likely the best you can achieve – assuming that code has not spread to other computers around you yet.
Obviously the traditional way of creating signatures is not working and needs to be revised. New approaches need to be invented; new weapons are needed for us to fight this battle and have some chance of turning the tables.
Network Box’s Z-Scan
About a year ago Network Box announced a new AV, which we call Z-Scan.
Z-scan takes an entirely new approach, based on statistical observations, which allows us to automate the process of creating and releasing signatures, thus reducing the entire cycle to a few seconds. The idea behind Z-scan is that certain things are malicious in nature and it is irrelevant what they truly are.
Network Box has deployed an extensive network of malware traps around the globe;these are email addresses that do not belong to a person, and there is no reason why they would ever receive a legitimate email. Therefore, anything arriving to these traps is either spam or malware.
How Z-Scan Works
When a piece of code is stopped by one of these traps, it is analyzed with three different traditional antiviruses. If these do not find anything, the assumption is that this code is malware – but it is new, it is a zero day attack, by definition it is something no one has yet seen. Hence, the system automatically creates a unique identifier, a hash, and distributes that via our cloud system to all our regional centers.
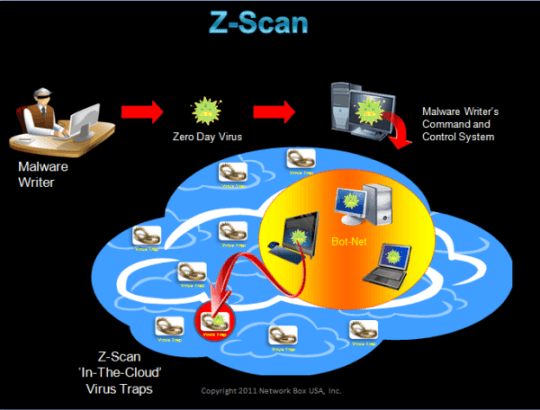
When a Network Box client, e.g. a bank, receives the same piece of code and the antiviruses do not find anything, this box creates the same unique identifier (same file, same algorithm yield same hash) and queries the regional center automatically with that hash. The regional center replies positively with a confidence factor that reflects how many times that same code has been seen. At this point, the bank box will block that code even though it does not know what type of malicious code it is. The reason why it blocks it is that this code was seen in a malware trap a few seconds earlier. The odds that it’d be legitimate are statistically zero and attaching an official name to that piece of code is irrelevant. What is, instead, very relevant is that it needs to be stopped – immediately. And that’s the approach Z-scan takes.
To provide an idea of the relevance of this system, one needs to keep in mind that once the traditional antivirus has the ‘official’ signature for that piece of code, the hash is removed from Z-scan, to ensure this is always running very fast. Therefore, the number of hashes in Z-scan is a measure of the number of pieces of malware in the wild that traditional antiviruses are not yet properly catching. If you click here, you can find the latest measures of the number of hashes. Scroll to item #7 and you will see the number of signatures running in Z-scan in real time. At the time I am writing this post, that number was above 150,000. This means that right now there are over 150,000 pieces of malware circulating on the Internet that traditional antivirus technologies are not yet catching. And hackers are counting on that to be able to bypass your security system(s). Z-Scan remedies that by stopping this malware with its new statistical approach.
Photo by Jonathan Borba on Unsplash