It Could Happen to Anyone
On Friday, 2nd November 2018, I received an email from the mailbox of one of our resellers (see below), inviting me to click on a link to open a secure message.
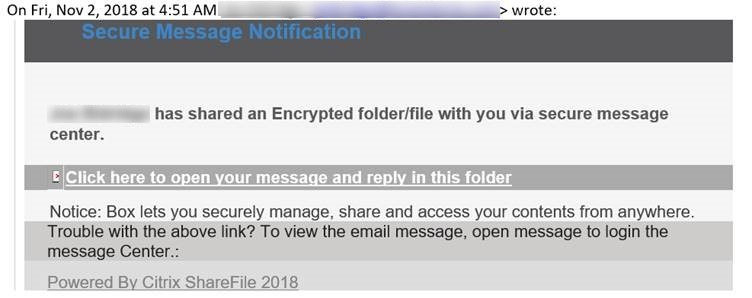
Now, when it comes to sharing private information in the US, this is a common practice. And although it is a practice I personally discourage for Network Box because we have our own internal sharing system called boxoffice, when someone sends me such a message, I can’t just simply ignore it. However, being that skepticism and caution are an inherent part of what I do for a living, I wrote back to the sender asking “Hey, is this actually a message YOU sent? Is it legitimate?” As I was rushing many other things, short of calling the guy in person, I figured this would be sufficient.
Within a few minutes, I received this reply, “The message is auto protected and can be easily revealed through open message button. you might be prompted to login through your email address portal. complete sign verification to open file. I believe you would definitely be interested. Thank you.”
This email too came from the same sender’s mailbox.
Given what we do as a company, it was actually easy for me to asses (1) that both messages were indeed sent from Office 365, and (2) it was actually what the sender was using.
And while I was still suspicious of the whole thing, and I felt the reply was rather too generic, I should’ve called the guy, asked what he was trying to send me, and why he wasn’t using boxoffice. But, I was in a hurry, and so, I clicked. Never should I have done that. I knew immediately, the moment I clicked, that I had done something I never should’ve.
That simple click caused mayhem. It stole my Outlook password and the list of all email recipients to whom I had ever written an email.
Yes, I immediately logged myself off from all the O365 sessions at once – iPhone, laptop, office workstation – all of them. Yes, I then changed my password. However, it was already too late. Such attacks are automated, and automation moves at a speed that humans simply can’t match. The script had already created a new admin account in our O365 system, somehow bypassing the 2 factor, and stayed dormant for 24 hours. At 1 PM the next day, it started sending out emails to all the recipients it had stolen from my Outlook. It took us a good hour, with the help of MS, to stop the whole thing. We had to log everybody out, stop the ability to login, remove all outgoing emails, and ensure everyone in the company changed their passwords, ensuring everyone used 2 factor, of course.
Lesson learned?
Phishing is getting smarter and smarter. And it will continue to get smarter and smarter.
I do this for a living, I have done it for almost two decades. I know what phishing is and how you can easily become a victim. My antennas are up all the time. I teach our clients how to spot a phishing email. And yet, because I was rushing, because the emails came from the mailbox of a user I was familiar with (and whose mailbox had been compromised), because maybe I had not slept well, because I am only human, who knows. Whatever the reason, I made the fatal mistake of clicking, and fell victim myself to something I always teach clients how to avoid.
The moral of this story? If it looks suspicious, it probably is. Don’t click.
Report. Delete.
Delete. Report.
Just don’t click.